10 Key Differences Between a GSOC and a Central Station
Aug 12, 2025
Today’s security threats are more complex and fast-moving than ever before, requiring stronger, more adaptive tools to manage risk. But choosing the right approach to monitoring your people and facilities can be challenging.
The evolution of monitoring solutions has evolved from a reactive, “sit and stare” function to one reflecting a more proactive, intelligence-led approach for enterprise-wide risk management. Over the last decade, this transformation has been hyper-fueled by COVID-19, hybrid work adoption, the convergence of cyber and physical security, and the adapting threat landscape, among others. Learn how the modern GSOC has transformed over the past decade.
For companies looking to identify and respond to risks in real time, two of the most common ways is through either a Central Station or Global Security Operation Center (GSOC), both of which provide the same base-level functions but can vary drastically in terms of additional levels of support. While central stations may suit smaller sites and support basic security functions, GSOCs deliver a more advanced, proactive, and integrated approach for complex security needs.
So, let’s break down the key differences between a GSOC and Central Station to better understand the best fit for your organization:
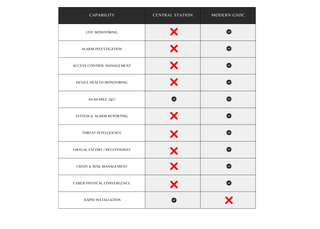
Monitoring and Alarm Investigation
Central Station: Simply escalates triggered alarms via call trees without oversight of video, access control, or other systems, which can often lead to false dispatches and associated penalties.
Modern GSOC: Delivers continuous 24/7 monitoring with integrated access to video management, access control, and other security technology systems. Investigates every alarm in real time, leveraging video context to verify triggers before escalating, eliminating false alarms often caused by held doors or faulty equipment.
Access Control Management
Central Station: No oversight or administrative control over user management, access levels, or remote access support.
Modern GSOC: Full oversight of user credentials, badge provisioning/de-provisioning, and policy enforcement. It can also facilitate remote unlocking and forced-entry events through direct system integration.
Device Health Monitoring
Central Station: Doesn’t track equipment status and relies on reactive alerts or customer reports.
Modern GSOC: Incorporates device monitoring to flag device malfunctions, log health metrics, and trigger automated maintenance dispatches all before failures hinder security.
Employee Support Availability
Central Station: Typically lacks real-time employee support.
Modern GSOC: Offers around-the-clock employee care, empowering operators to assist with lockouts, badge issues, system changes, and emergency coordination at any time of day.
System & Alarm Reporting
Central Station: Limited reporting tools due to a lack of interconnectivity between security technology systems.
Modern GSOC: Delivers robust analytics such as alarm trend tracking, device performance stats, and optimization recommendations backed by data from a variety of systems.
Threat Intelligence
Central Station: Not responsible for identifying threats outside of your physical locations.
Modern GSOC: Integrates global and regional threat intelligence such as weather, geopolitical incidents, and local crime into monitoring feeds to provide more situational awareness for your office, travelers, or remote employees.
Virtual Escort & Receptionist
Central Station: Offers no capability for virtual escort or interaction with visitors.
Modern GSOC: Leverages VMS, intercom, and access control to provide virtual escorts or remote reception, staying on-call with late night staff or vetting unbadged visitors in real time.
Incident Response
Central Station: Does not support incident response beyond notification.
Modern GSOC: Develops and executes enhanced standard operating procedures to respond to incidents in real time above and beyond notification. This can include distributing mass notification, contacting local authorities, or dispatching guards in real time.
Cyber-Physical Convergence
Central Station: Operates in siloed physical environments.
Modern GSOC: Demonstrates a strong grasp of cybersecurity principles and contributes to broader initiatives such as password rotation, vulnerability identification, and rapid detection of unusual system behavior indicative of malicious activity.
Installation & Onboarding
Central Station: Simple, fast setup that typically goes live shortly after installation.
Modern GSOC: Requires in-depth onboarding such as security audits, policy design, custom workflows, PSIM integrations, test plans, and phased deployment. Outsourced models can significantly reduce the timeline compared to in-house builds.
Outsourcing your GSOC: The Smarter Approach
Is GSOC the right move for you? Now that you better understand the differences, the good news is that you don’t have to build one alone.
For many small to mid-sized companies, outsourcing is a smarter, more scalable solution. If your team lacks in-house expertise, operates lean, or struggles with outdated tech, an outsourced model gives you instant access to experienced professionals, advanced technology, and 24/7 coverage without the heavy lift.
An outsourced GSOC provides all the functionality of a purpose-built center: threat intelligence, 24/7 monitoring, badge and access control management, virtual reception, and alarm investigation without the capital investment and staffing burden.
With a shared-resource model, you can:
- Start quickly with prebuilt infrastructure
- Easily scale with your business needs
- Gain instant access to a team of seasoned professionals
- Receive customizable workflows and reporting
- Focus your internal team on strategic security decisions instead of day-to-day administrative support
Not sure if it’s right for you? This blog outlines three clear signs your organization could benefit from an outsourced physical security model.
We’re here to help you explore whether outsourcing your GSOC makes sense for your organization. Contact us at info@northlandcontrols.com to learn more.